 Assess your data environment to detect vulnerabilities and design remedial actions
Assess your data environment to detect vulnerabilities and design remedial actions
Make a complete list of hosts and network devices, categorized all the data.
Make a network topology to fully cover your business environment.
Review security policies and best practices.
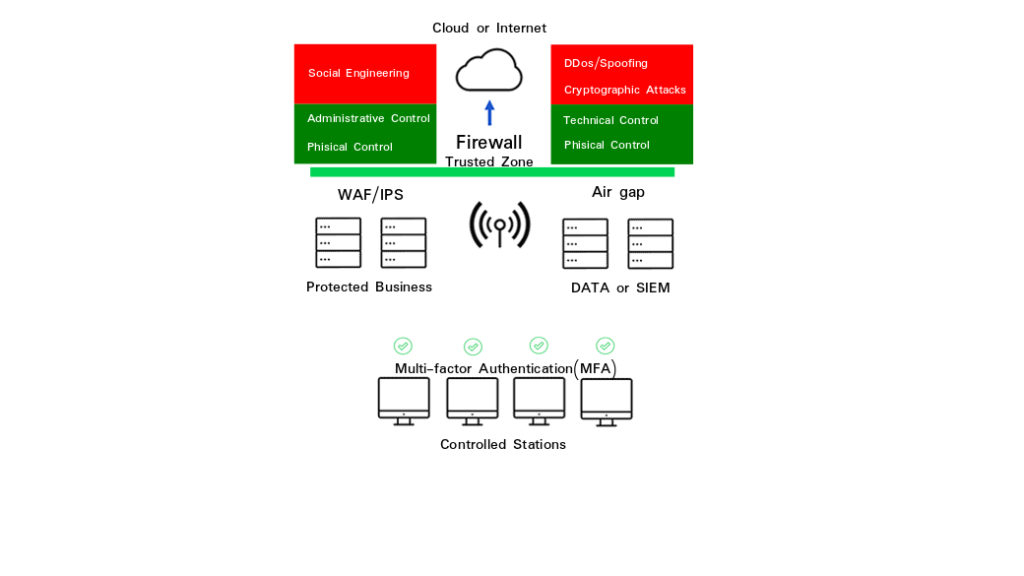
Security assessment, also known as vulnerability assessment is processing designed to assess computers, networks, or systems for known weaknesses. In plain words, this processing is used to discover the weaknesses of a given system recorded in a predefined scanning system. They are utilized in the identification and detection of vulnerabilities arising from misconfigurations or flawed programming within a network-based asset such as a firewall, router, web server, application server, etc. Modern vulnerability scanners allow for both authenticated and unauthenticated scans.
- Authenticated scans allow for the scanner to directly access network-based assets using remote administrative protocols such as secure shell (SSH) or remote desktop protocol (RDP) and authenticate using provided system credentials. This allows the vulnerability scanner to access low-level data, such as specific services and configuration details of the host operating system. It’s then able to provide detailed and accurate information about the operating system and installed software, including configuration issues and missing security patches.
- Unauthenticated scans is a method that can result in a high number of false positives and is unable to provide detailed information about the assets operating system and installed software. This method is typically used by threat actors or security analysts trying to determine the security posture of externally accessible assets.
