1. Why a netfilter instead of virtual interface
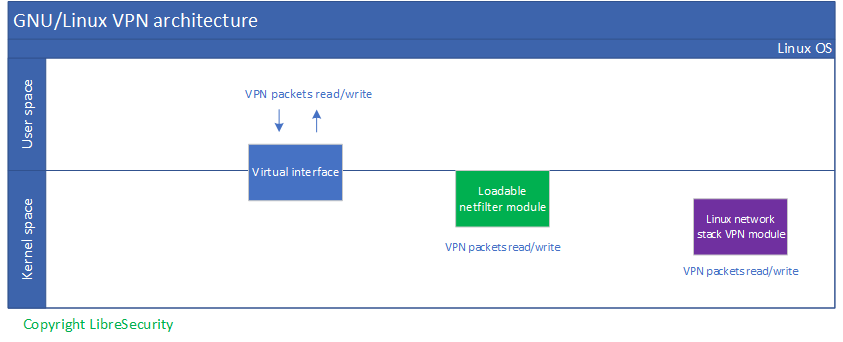
Typically, VPN architecture on GNU/Linux are using three different solutions.
The most common and developer friendly one is TUN/TAP interface from Linux kernel. The TUN/TAP interface can be read/wrote by VPN client, and manage its life span through the whole VPN session.
The native Linux network stack VPN module is used for high performance VPN architecture, and not user friendly in the development phase because of its complexity and native integrated in Linux network stack.
The most efficient way is loadable netfilter VPN module which embedded with VPN ingress and egress traffic engine. This solution can be benefit for both performance and development friendly.
2. Netfilter module mechanism
When netfilter module used as VPN packets filtering, netfiler can provide multi-hook for packets processing and build internet firewalls based on stateless and stateful packet filtering.
What are Netfilter Hooks
There are five netfilter hooks that programs can register with. As packets progress through the stack, they will trigger the kernel modules that have registered with these hooks. The hooks that a packet will trigger depends on whether the packet is incoming or outgoing, the packet’s destination, and whether the packet was dropped or rejected at a previous point.
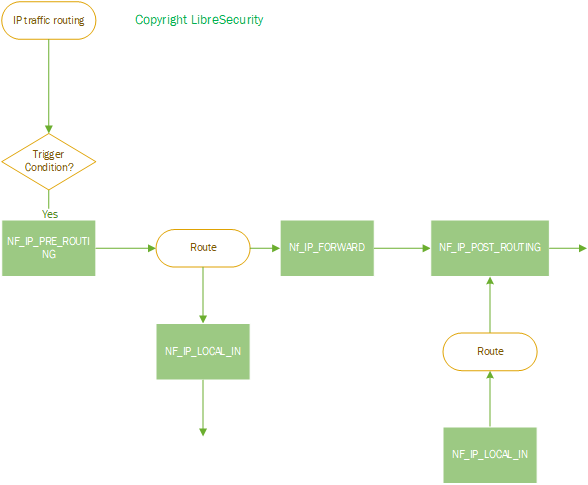
The following hooks represent various well-defined points in the networking stack:
NF_IP_PRE_ROUTING: This hook will be triggered by any incoming traffic very soon after entering the network stack. This hook is processed before any routing decisions have been made regarding where to send the packet.
NF_IP_LOCAL_IN: This hook is triggered after an incoming packet has been routed if the packet is destined for the local system.
NF_IP_FORWARD: This hook is triggered after an incoming packet has been routed if the packet is to be forwarded to another host.
NF_IP_LOCAL_OUT: This hook is triggered by any locally created outbound traffic as soon it hits the network stack.
NF_IP_POST_ROUTING: This hook is triggered by any outgoing or forwarded traffic after routing has taken place and just before being put out on the wire.
Netfilter XFRM has hooks ‘truct list_head nf_hooks[NPROTO][NF_MAX_HOOKS]’ to store data structure, one for protocols, the other for hook entries.
Every hook entry functions have their own status code, will provide to filtering program to process packets:
NF_ACCEPT: All green and continue to process,
NF_DROP: Abandoned,
NF_STOLEN: Processed, not proceeding to next,
NF_QUEUE: Queued packets, can be processed by user program,
NF_REPEAT: Repeat hook program.
3. Netfilter processing modules
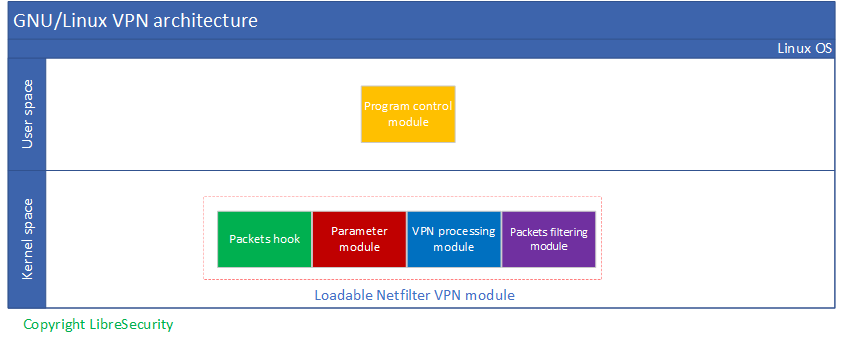
We could divide netfiler modules into four modules inside kernel space: Packets hook, parameter module, VPN processing module, and packets filtering module. And control program can run as a single control unit.
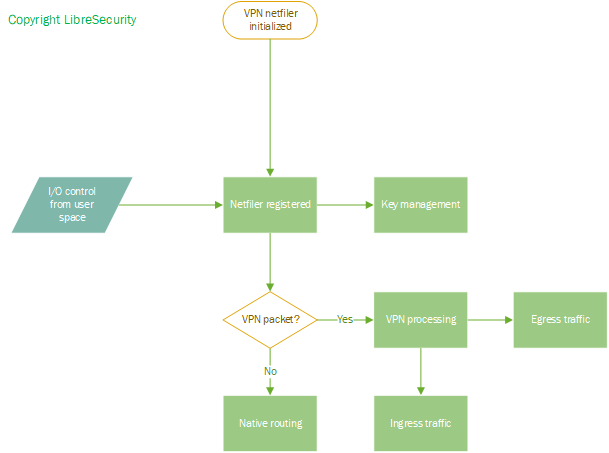
4. Traffic flow inside Netfiler module
When loadable netfilter module is initialized, the user space control program can send parameters and I/O controls to it.